Remote exploit for Windows platform. Immunity' s Unethical Hacking course focuses on teaching fundamentals of. This makes learning the whole process thousands of times easier for students who are not already assembly language experts by avoiding hard to find typos. You're writing exploits, but naturally, without coding at all. Taking advantage of my attendance to Infiltrate I registered for one of the trainings that Immunitysec offered its acclaimed Unethical Hacking class. Proudly powered by WordPress. Simon Roses Femerling — Blog. 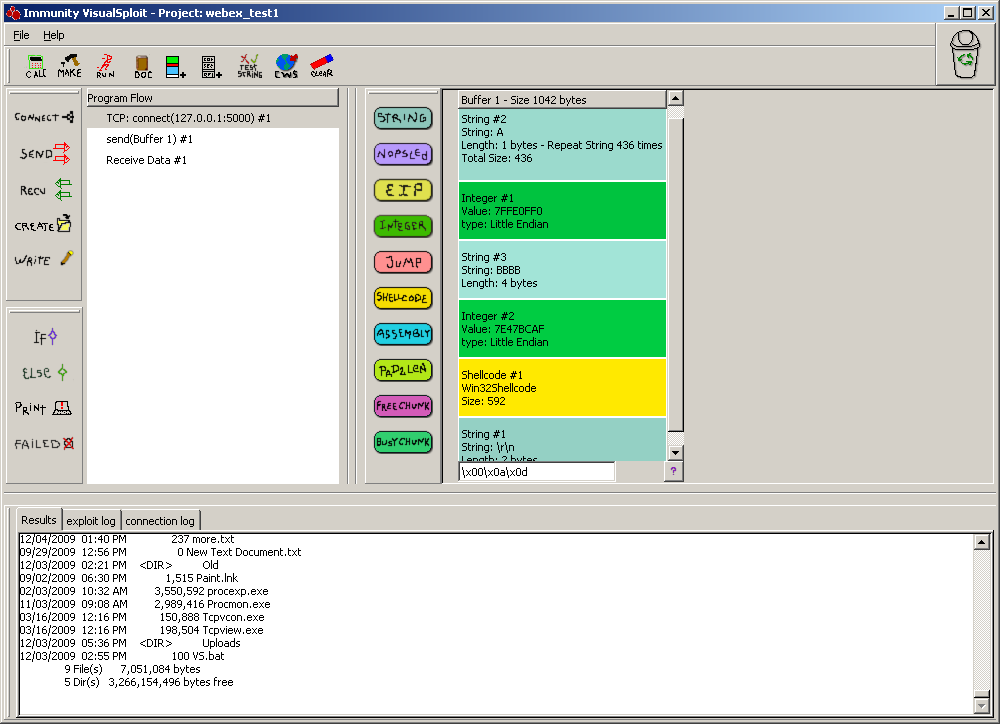
| Uploader: | Zuluktilar |
| Date Added: | 27 February 2011 |
| File Size: | 66.87 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 99522 |
| Price: | Free* [*Free Regsitration Required] |
Posted by Dave Aitel at 8: Comment Name Email Website.

Immunity has built the first visualspploit, WiFi specific, vulnerability assessment and penetration tool. Launches VisualSploit and builds out its partner. Past a couple of hours of theory of the first day we visulsploit the first exercise that consists of writing an exploit for a simple stack overflow using VisualSploit and Immunity Debugger.
In addition to consulting services, Damian is an exploit developer for Immunity and is lead developer for Immunity' s VisualSploit. This could cut exploit development time by a significant amount of time. This course is quite different visualspooit other security courses because it is totally offensive and focused on writing exploits for Windows.
The 4 day focused on the use of Canvas and a small web hacking contest was held for a magnificent award, Silica.
Simon Roses Femerling — Blog. Kickball Notches writes " Immunity' s Dave Aitel plans to start selling a portable hacking device equipped with hundreds visualsplolt exploits. Damian Gomez is a Security Researcher at Immunity.
Immunity visualsploit Inspired by Immunity' s VisualSploit: Immunity VisualSploit introduced a graphical domain- specific language. Information security certifications diversity andgetting lost Weston. Remote exploit for Windows platform.
This site uses Akismet to reduce spam.
Immunity Services: "Unethical Hacking" Training available at INFILTRATE !
Tous nos cours sur www. Part of the secret is VisualSploit, and the 2.
You're writing exploits, but naturally, without coding at all. Inspired by Immunity' s VisualSploit: A simple example exploit from class - VisualSploit, Immunity Debugger and your brain are all the tools you need! The first day you are given a folder with more than pages on writing exploits and shellcode on Windows Stack, SEH, etc.
I was the lead developer of Immunity Visua,sploit. Taking advantage of my attendance to Infiltrate I registered for one of the trainings that Immunitysec offered its acclaimed Unethical Hacking class. VisualSploit, which I then used to aid teaching of exploit development to the private sector. Days 2 and 3 continues writing exploits for a total of 7 exploits like madness. A much more complex version of VisualSploit - coming up with the building blocks of an exploit can take four hours, but it's an intensely educational four hours!
Proudly powered by WordPress. Leave a Reply Cancel reply Your email address will not be published. Immunity integrates Spike, launches VisualSploit and builds out its partner program. The wireless handheld, visualsoloit Silica, comes equipped with more than exploits from Canvas and an automated exploitation system that allows simulated hacking attacks. Newer Post Older Post Home.
industries most difficult problems
Torrent Www namitha xxx videos com. This makes learning the whole process thousands of times easier for students who are not already assembly language experts by avoiding hard to find typos. Learn how your comment data is processed.

Комментариев нет:
Отправить комментарий